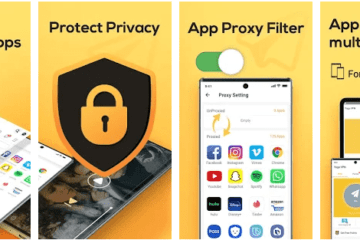
Download InviZible Pro get access to blocked and hidden online resources
Shield your gadget from perilous locales, dispose of irritating promotions and following, gain admittance to obstructed assets in your country!
InviZible Pro: increase your security, protect you.
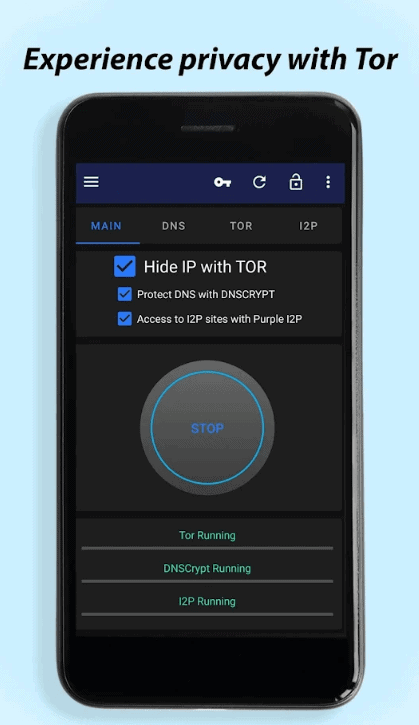
Invisible Pro incorporates the notable modules DNSCrypt, Tor and Purple I2P. These modules are utilized to accomplish most extreme security, protection and convenience of the Internet.
Invisible Pro can utilize root, if your gadget has root advantages, or uses a nearby VPN to convey Internet traffic to Tor, DNSCrypt and I2P organizations.
Elements:
* No root required
* Hides area and IP
* Unblocks the limited web content
* Prevents following
* Allows admittance to stowed away organizations
* ARP ridiculing location
* Built-in firewall
* Tethering upheld
* Material plan subject
Simply start Invisible Pro, and you abandon a straightforward client to an undetectable one, who is truly challenging to track down, hinder or force pointless items and administrations as omnipresent publicizing on.
In any case, assuming you need to deal with the program and your Internet association – no issue! Invisible Pro gives admittance to countless both basic and expert settings. You can without much of a stretch design Invisible Pro itself, just as its modules – DNSCrypt, Tor and Purple I2P, to fulfill the most non-standard prerequisites.
Invisible Pro is an across the board program. In the wake of introducing it, you can without much of a stretch erase the entirety of your VPN applications and advertisement blockers. As a rule, Invisible Pro works better, is more steady, and quicker than free VPNs. It doesn’t contain advertisements, bloatware and doesn’t spy upon its clients.
Invisible Pro squares ipv6 because of some security issues with this convention and the Invisible application.
So what are those three modules, and what do they accomplish?
DNSCrypt
DNS is utilized by most applications to make an interpretation of space names into IP locations to track down a far off worker with the site that you need to visit. However, this correspondence isn’t scrambled and can be utilized by assailants. DNSCrypt scrambles and confirms DNS traffic, subsequently forestalling DNS following and ridiculing.
* Encrypts DNS demands
* Protects against DNS ridiculing
* Blocks ads¹
* Protects against perilous and phishing sites¹
* Can hinder “grown-up” sites¹
* Hides visited destinations from your supplier
* Prevents a few sorts of asset locks
¹ Depending on the chose decryption worker
Peak
Peak encodes Internet traffic and shrouds your genuine area. It utilizes a large number of PCs all throughout the planet to veil your IP address and forestalls movement following to protect your security and obscurity. Pinnacle likewise gives admittance to onion administrations. These are destinations that are in a totally covered up network without control.
* Encrypts Internet traffic
* Prevents destinations locking
* Can give protection and timelessness
* Provides admittance to “onion” destinations
Purple I2P
The Invisible Internet Project (I2P) is a secret mysterious organization. It incorporates a great many PCs dispersed all throughout the planet. Purple I2P scrambles the traffic of your gadget and sends it through these PCs to guarantee protection and obscurity. Start I2P to get to I2P destinations and other Invisible Internet stowed away administrations.
* Encrypts Internet traffic
* Provides admittance to the secret mysterious organization Invisible Internet and “i2p” destinations
Keeps privacy, prevents tracking, gets access to blocked and hidden on-line resources.
Invisible Pro uses DNSCrypt, Tor and Purple I2P to achieve maximum security, privacy and comfortable use of the Internet.
DNS is used by most applications to translate domain names into IP addresses to find a remote server with the site that you want to visit. But this communication is not encrypted and can be used by attackers. DNSCrypt encrypts and authenticates DNS traffic, thus preventing DNS tracking and spoofing.
Tor encrypts Internet traffic and hides your actual location. It uses thousands of computers around the world to mask your IP address and prevents activity tracking to preserve your privacy and anonymity. Tor also provides access to onion services. These are sites that are in a completely hidden network without censorship.
The Invisible Internet Project (I2P) is a hidden anonymous network. It includes thousands of computers distributed around the world. Purple I2P encrypts the traffic of your device and sends it through these computers to ensure privacy and anonymity. Start I2P to access i2p sites and other Invisible Internet hidden services.
InviZible Pro can use root, if your device has root privileges, or uses a local VPN to deliver Internet traffic to Tor, DNSCrypt and I2P networks.
Read more about “How to Root Android In 2021 – Vmos Virtual Machine Operating System!
Premium feature:
* Material design night theme
– InviZible Pro does not support ipv6 at this time.